Explain Different Indexing and Hashing Techniques
The mapped integer value is used as an index in the hash table. Hashing technique is used to calculate the direct location of a data record on the disk without using index structure.
What Is The Difference Between Indexing And Hashing Pediaa Com
The hash code which is an integer is then mapped to the fixed size we have.
. N Memory types have different characteristics in terms of l Persistent vs. There are two types of Hash Tables. Collisions are bound to occur no matter how good a hash function is.
An Open-addressed Hash Table is a one-dimensional array indexed by integer values that are computed by an index function called a hash function. 123 124 135 1267 2378 9087 and hash table size is 10 0-9 indices Now If our hashing function is F xdigits in x Then 123-3 124-3 135-3 1267-4 2378-4 9087-4. Open-addressed Hash Tables and Separate-Chained Hash Tables.
In simple terms a hash function maps a significant number or string to a small integer that can be used as the index in the hash table. The hash table will look like In the above example we can see though there are 10 indices only 2 are being used and the collision rate is too high. Generally these hash codes are used to generate an index at which the value is stored.
MD5 - An MD5 hash function encodes a string of information and encodes it into a 128-bit fingerprint. Hashing uses hash functions with search keys as parameters to generate the address of a data record. Hkk mod m This gives the indexes in the range 0 to m-1 so the hash table should be of size m This is an example of uniform hash function if value of m will be chosen carefully.
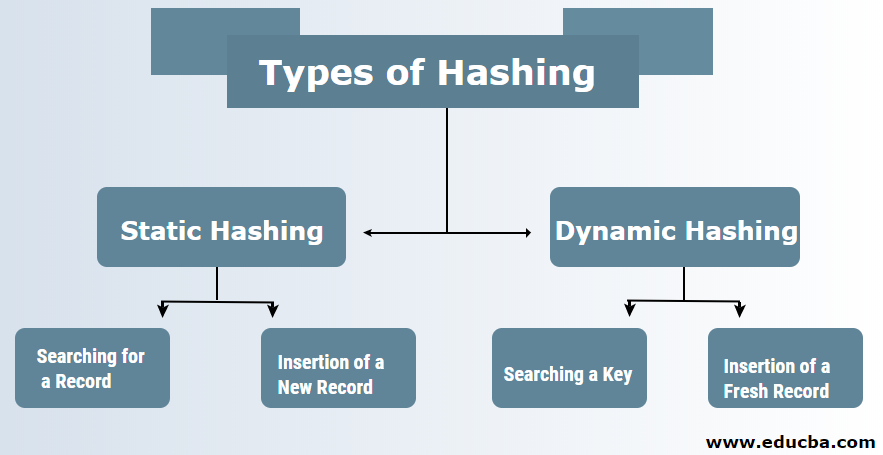
Open Hashing Separate chaining Closed Hashing Open Addressing Liner Probing. Two types of hashing methods are 1 static hashing 2 dynamic hashing. Hence to maintain the performance of a hash table it is important to minimise collisions through various collision resolution techniques.
Hashing is an effective technique to calculate the direct location of a data record on the disk without using index structure. For example if the list of values is 1112131415 it will be stored. The index records have the search key and a pointer to the actual record on the disk.
CS425 Fall 2013 Boris Glavic 114 Silberschatz Korth and Sudarshan DBMS Storage n Modern Computers have different types of memory l Cache Main Memory Harddisk SSD. This method generally used the hash functions to map the keys into a table which is called a hash table. A data structure where the data is stored based upon its hashed key which is obtained using a hashing function.
Hashing is type of primary file organization which provide very fast access to record in file on search condition. Database D Basic 15 minutes. 123 124 135 have collided.
Hashing is a technique which uses less key comparisons and searches the element in On time in the worst case and in an average case it will be done in O1 time. Another difference between indexing and hashing is that the. In this the number of records in the index table is same as the number of records in the main table.
Static Hashing - Index scheme forces us for traverse an index structure while hashing technique avoid this. In the static hashing the resultant data bucket address will always remain the same. SlideShare uses cookies to improve functionality and performance and to.
The pair is of the form key value where for a given key one can find a value using some kind of a function that maps keys to values. It makes searching faster. It needs more space to store index record itself.
Indexing uses data reference that holds the address of the disk block with the value corresponding to the key while hashing uses mathematical functions called hash functions to calculate direct locations of data records on the disk. A Separate-Chained Hash Table is a one-dimensional array of linked lists indexed. In this technique data is stored at the data blocks whose address is generated by using the hashing function.
Say the set of keys are. Searches may occur by movie title director studio or star and should be able to retrieve related information. It allows search without using indices.
Indexing and Hashing Basic Concepts Ordered Indices B-Tree Index Files B-Tree Index Files Static Hashing Dynamic Hashing Comparison of Ordered. Sequential access l Size l Price this usually determines size n Database systems are. Hence this is also a major difference between indexing and hashing.
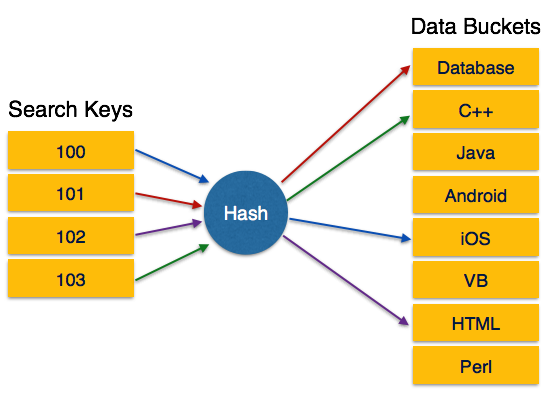
Let a hash function H x maps the value at the index x10 in an Array. Bucket A hash file stores data in bucket format. The key which is used to identify the data is given as an input to the hashing function.
The dense index contains an index record for every search key value in the data file. Volatile l Speed random vs. Database design file structures indexing and hashing methods.
The efficiency of mapping depends on the efficiency of the hash function used. Hashing Function Methods Hashing Methods Division Hash Method The key K is divided by some number m and the remainder is used as the hash address of K. In hash tables you store data in forms of key and value pairs.
There are majorly 2 methods for handling collisions. This type of file system is hash file. Hashing is a type of a solution which can be used in almost all situations.
Bucket is considered a unit of storage. It is done for faster access to elements. 10 minutes You have been requested to design a database for fans of old movies.
In this article we have explored the idea of collision in hashing and explored different collision resolution techniques such as. Hashing is a technique or process of mapping keys values into the hash table by using a hash function. Data bucket Key Hash function Linear Probing Quadratic probing Hash index Double Hashing Bucket Overflow are important terminologies used in hashing.
Hashing in a Database Management System is a procedural approach applied to rationally find the position of the required data instead of creating new indexes or using the existing index structures of the database system by making use of dedicated methods called the Hash functions or Buckets to search the specific data from the disk memory as opposed to the. The memory location where these records are stored is known as data bucket or data blocks. MD5 is often used as a checksum to verify data integrity.
It can be used to create index structure. There are many different types of hash algorithms such as RipeMD Tiger xxhash and more but the most common type of hashing used for file integrity checks are MD5 SHA-2 and CRC32.
What Is The Difference Between Indexing And Hashing Pediaa Com

Comments
Post a Comment